A security profile in Sage X3 is an essential component of the system’s security framework, allowing you to control and manage access to various resources, data, and functionality within the Sage X3 ERP (Enterprise Resource Planning) system. Security profiles are used to set and enforce user-specific rights and limits, ensuring that individuals or roles in your organization can only access and perform tasks that are related to their responsibilities.
These profiles are highly customizable, allowing administrators to configure rights according to the module, data, and actions that users can access. By defining security profiles, organizations can maintain data integrity, protect sensitive information, and agree with regulatory requirements, which helps to enhance the overall security and transparency of their Sage X3 system.
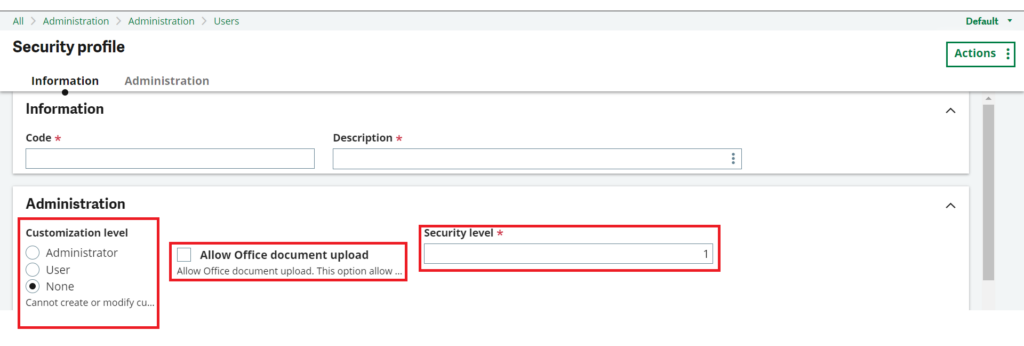
The following information is entered while creating a security profile:
Code
It refers to a unique identifier used to uniquely identify a security profile. This code is required for the system to reference and manage certain security profiles. It enables administrators to distinguish and deal with various security profiles, making it easier to assign and restrict access permissions for users or roles based on these codes. The code is essentially a label or reference used to simplify security profile administration in the Sage X3 ERP system.
Description
It is a field or attribute that provides a quick yet informative explanation of a security profile. This description helps to provide extra context and details about the security profile’s purpose or role. It assists users and administrators in understanding the function of the profile, making it easier to find the proper profile for a given purpose or job inside the system. Individuals who need to work with security profiles in Sage X3 will find the description field useful.
Customization level
Defines the level of Customization a user can perform on pages:
* None: No customization is allowed.
* User: Customization is allowed, but only on a page that is dedicated to the user.
* Administrator: the user can modify the authored page shared by several users.
Allow Office document upload
This setting determines whether a user has the capability to upload Office documents within a system. By default, this feature is deactivated as a security precaution to safeguard against potentially harmful Office documents. To enable the user to upload Office documents, this setting must be activated. This feature allows users to upload and work with Office files but should be managed carefully to maintain system security.
Security Level
“Security Level” represents a numerical rating assigned to each security profile, typically ranging from 0 to 99. This numeric level plays a critical role in determining a user’s authority to create or modify security profiles. The rule is that a user can only create or modify security profiles that have a security level higher than the user’s own security profile. Put simply, a user with a security level of 1 is restricted to viewing and managing security profiles with security levels of 2 and above. This hierarchy ensures that higher-level security profiles are controlled by users with the appropriate clearance, enhancing security and access control within the system.
Authorizations
This grid displays a list of predefined codes as well as their descriptions. Each code is an identifier for a certain controlled entity, and it is accompanied by filters that determine its behavior. These codes are used to categorize and manage controlled entities, making it easier to understand their function and the criteria that regulate them within the system.
For every code, you can select the checkboxes to define the access rights granted by the security profile. When a check box is cleared, the access right is denied. A user cannot provide access to codes for which he doesn’t have rights. If this is the case, the corresponding check boxes are disabled.
The access rights are the usual CRUD access (Creation, Read, Update, and Delete), plus an additional Execution right.
Associated roles
This section defines the roles that the security profile applies to. In this area, you can assign roles to the security profile, or you can use the roles management interface. However, a single role cannot be linked to multiple security profiles. If a role does not have an associated security profile, it means that the system sets no specific restrictions on that role.
Security profiles in Sage X3 are essential for controlling access to resources and data within the ERP system. They use unique codes and descriptions for clarity, and users must confirm to numeric security levels when modifying profiles. Roles are linked to security profiles to manage access, with each role associated with a single profile. When no security profile is assigned to a role, it operates without specific restrictions. These profiles are a key component of Sage X3’s security framework, safeguarding data integrity and ensuring compliance while providing personalized control over user access.
About Us
Greytrix – a globally recognized Premier Sage Gold Development Partner is a one-stop solution provider for Sage ERP and Sage CRM needs. Being recognized and rewarded for multi-man years of experience, we bring complete end-to-end assistance for your technical consultations, product customizations, data migration, system integrations, third-party add-on development, and implementation expertise.
Greytrix caters to a wide range of Sage X3 (Sage Enterprise Management) offerings – a Sage Business Cloud Solution. Our unique GUMU™ integrations include Sage X3 for Sage CRM, Salesforce.com, and Magento eCommerce along with Implementation and Technical Support worldwide for Sage X3 (Sage Enterprise Management). Currently, we are Sage X3 Implementation Partner in East Africa, Middles East, Australia, and Asia. We also offer best-in-class Sage X3 customization and development services, integrated applications such as POS | WMS | Payment Gateway | Shipping System | Business Intelligence | eCommerce, and have developed add-ons such as Catch – Weight and Letter of Credit for Sage X3 to Sage business partners, end users and Sage PSG worldwide.
Greytrix is a recognized Sage Rockstar ISV Partner for GUMU™ Sage X3 – Sage CRM integration also listed on Sage Marketplace; GUMU™ integration for Sage X3 – Salesforce is a 5-star app listed on Salesforce AppExchange.
For more information on Sage X3 Integration and Services, please contact us at x3@greytrix.com. We will be glad to assist you.

